Privacy, Identity and personal data are the new politics, religion andsex of after dinner fall outs
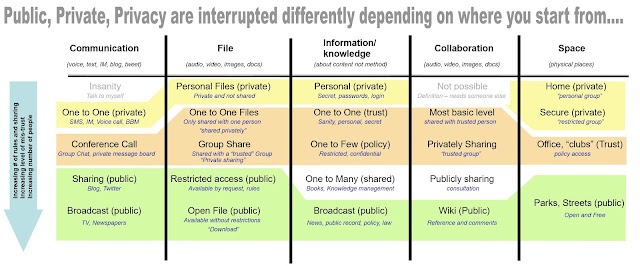
Ask a group of friends to define any of the following words:- private, privacy, trust, sharing, personal data, data, rights or context and whilst you may start the evening as friends; you may well end the evening questioning ideologies. Privacy, Identity and personal data have become the new politics, religion and sex conversation topics that we should not discuss. But why? My personal view is that, just like politics, religion and sex, we all start from different points (knowledge and mood today), with varying expectations (outcomes) and personal experiences (crosses to bare). This opinion piece is about the different starting points and not expectations or personal experience; as we get to read about expectations from daily FUD (Fear, Uncertainty and Doubt) articles that form fabulous NEWS headlines, and personal experiences as well, they’re personal. This opinion is not trying to convert or sway anyone from their trusted viewpoint; the purpose is to present a frame...