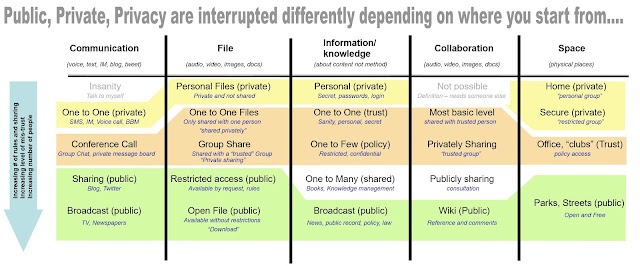
Assuming that “Identity,Trust and Privacy” fade [by fade I mean hard boundary (technical, permission, certificate) and soft boundary (time, relevance, reach)], is it useful to consider that your network [by which I mean consider the network in the widest possible sense: physical, six degrees, payment, access, codes, influence, reach, recommendation, LogIn, ID, FoF] edges should be defined by a propensity to risk. The lower risk desired the closer you need to be to the source. Is our frustration that those with the lowest risk have the highest authority and that I cannot enable my risk profile across my services?